How to find and eliminate MFA gaps in Microsoft 365
Finding security gaps is often a task that falls into the lap of a company’s IT department. Ensuring that users have implemented strong Microsoft Office 365 multi factor authentication methods is usually at the top of the list of priorities for IT admins. Unfortunately, pinpointing which employees have weak MFA configurations in the Microsoft admin portals can be time-consuming and not always easy. Let’s look at how one customer solved this challenge.
One customer’s successful elimination of Microsoft Office 365 multi factor authentication gaps
Our customer Daphne, an IT administrator at a leading insurance company, was asked to react quickly to resolve an issue. One of their partners had recently experienced a security breach, and the management team realized they were also at risk. The company needed to be 100% secure, so they asked Daphne to investigate and improve their Office 365 Multi Factor Authentication (MFA) methods. As an IT admin, Daphne was aware that weak or missing authentication methods could lead to a hacker gaining access.
She was worried that identifying which users had Microsoft Office 365 multi factor authentication methods that were weak would take too much time. While PowerShell scripts could be used, Daphne could not write PowerShell code, and there was no in-house expertise in her company. Daphne did not like the MFA reports that PowerShell generates. She found they needed a lot of manipulation before she could get a global view.
How to solve the problem
Daphne’s first decision was to move to the new Azure AD Multi-Factor Authentication which relies on Conditional Access policies. She had to set the proper policies to implement strong MFA, but doing this wouldn’t correct issues from the past. She knew that weak authentication methods would not be removed automatically.
Daphne needed to do some investigating to discover which employees had MFA and which ones didn’t, and then see which authentication methods they were currently using. If the employee MFA was enforced by the legacy per-user MFA, Daphne would have to go to the multi-factor authentication page and turn it off manually. Daphne’s company had over 1,000 employees, so she was worried about how long it would take her to accomplish this.
See the whole picture
Luckily, Daphne had recently purchased sapio365, a Microsoft 365 admin tool that is an alternative to PowerShell. It’s ideal for teams that need to solve challenges that seem impossible, all without relying on hard-to-find expertise. She had been using it to solve other IT issues but she was certain it could help her with this task.
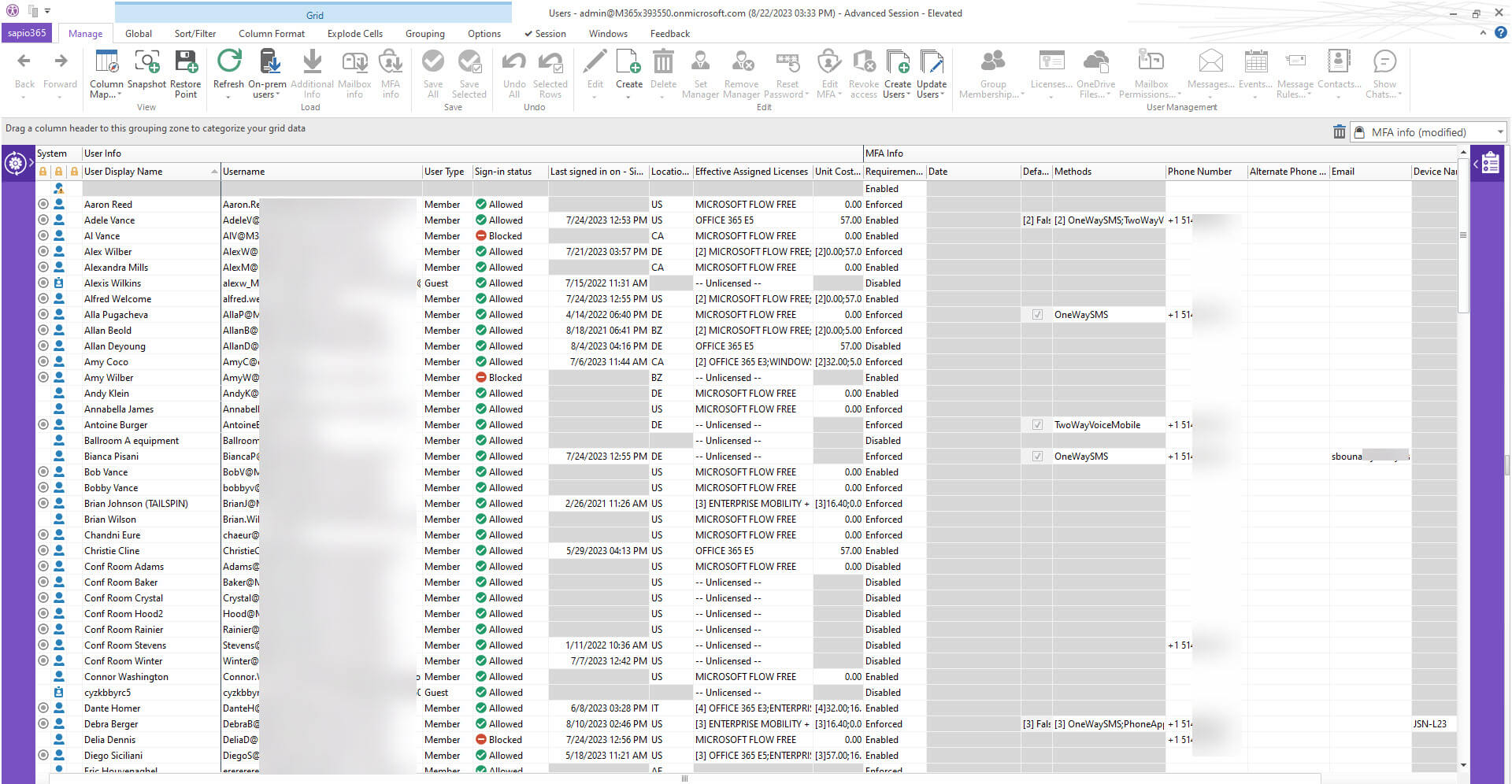
With sapio365, she could easily get a complete view of the MFA situation, including all users, the registered methods for each user, and their status on the legacy per-user MFA, without having to manipulate a lot of data.
Daphne started out by creating a view that would show her MFA information for each user to determine who had legacy per-user MFA. She quickly realized that the majority did.
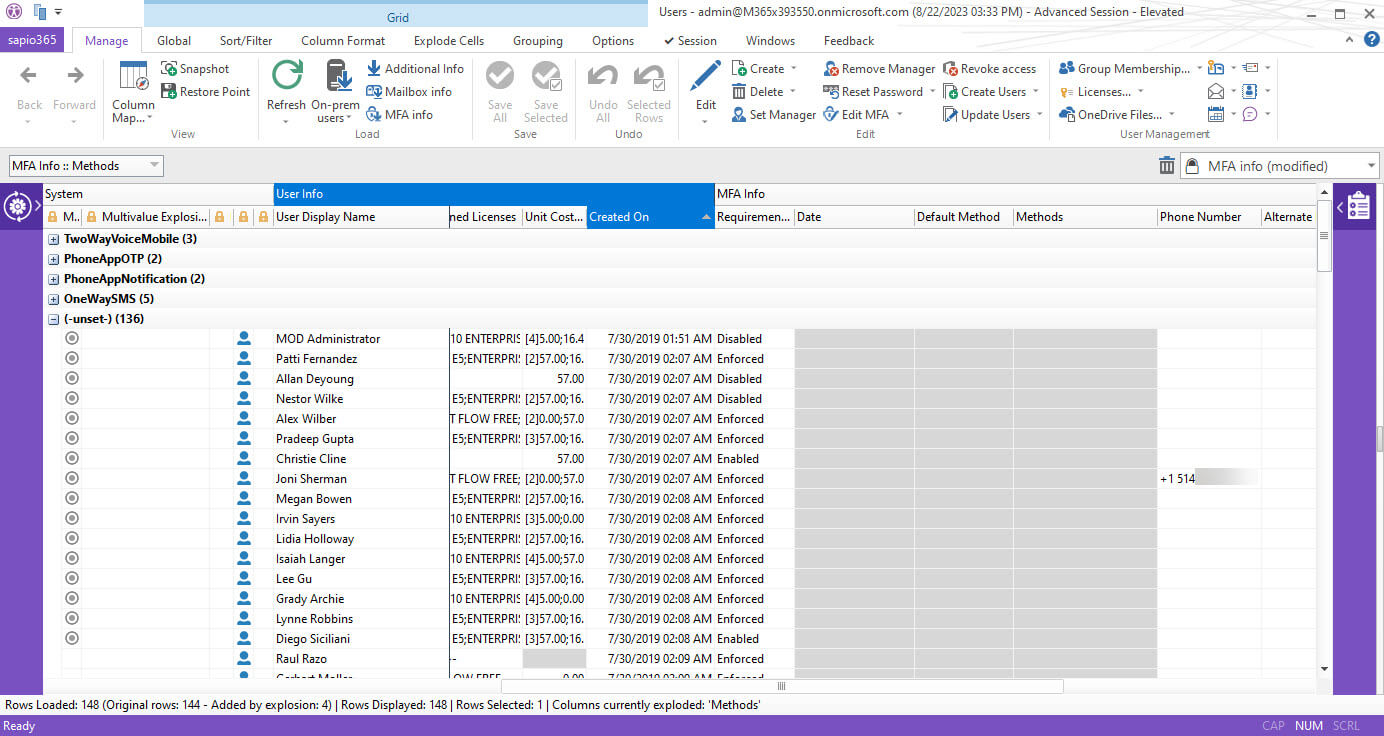
So, she arranged an organized view of all the authentication methods that were being used and by whom. She discovered that weak authentication methods, like SMS and phone calls were being used by many employees. Looking at her list, she found user accounts that were created a while ago and which had no authentication methods.
Quickly disabling the problem
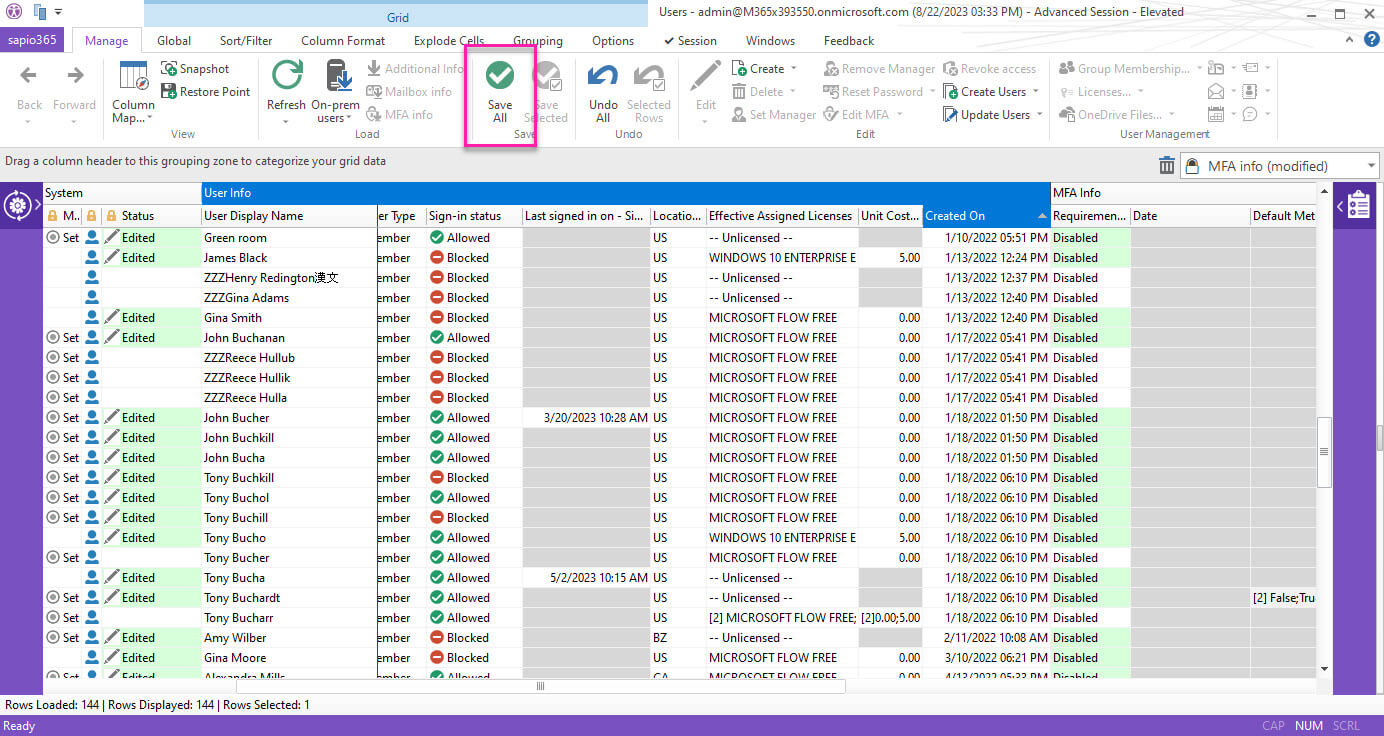
Daphne started by filtering out the users with disabled legacy per-user MFA and then selected the remaining users who were enabled or enforced. She previewed these accounts who were about to be disabled and once satisfied, she disabled in one click.
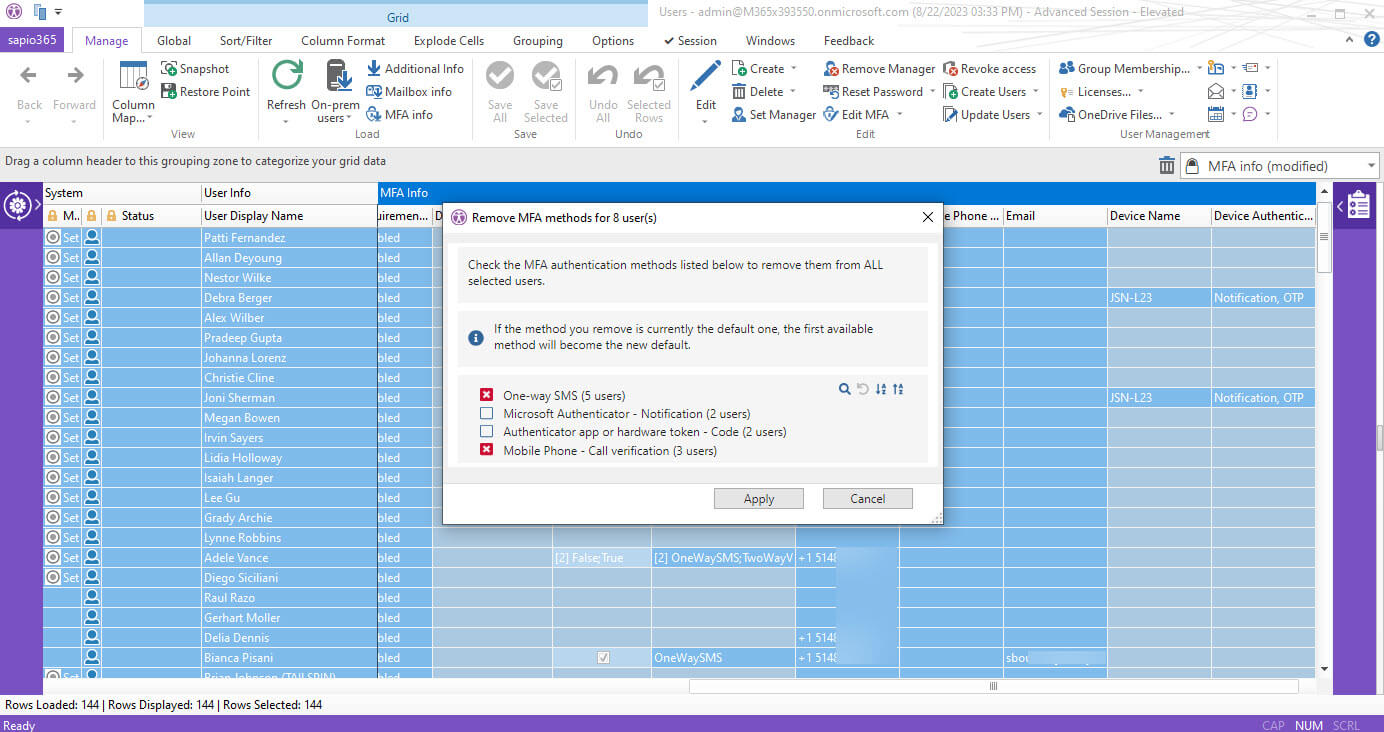
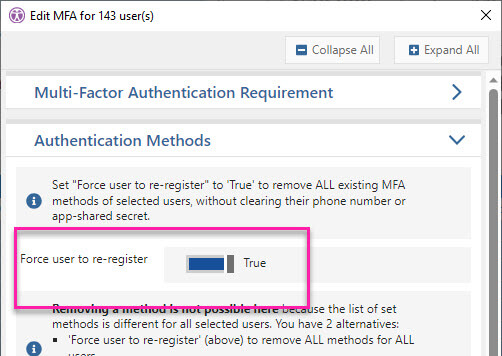
Now that the users with legacy per-user MFA were disabled, Daphne needed to remove the weak authentication methods from all the users. She selected the two methods, checked her preview and then removed them with one click.
Once the conditional policies were ready to be deployed, she would be able to force users without any authentication methods to register new ones from an approved list in one click in sapio365.
The next step was to check the accounts where the MFA had not been activated. In other words, where there were no methods set. She knew there may be some service accounts and shared mailboxes, so she looked for them and skipped them when she forced MFA re-registration.
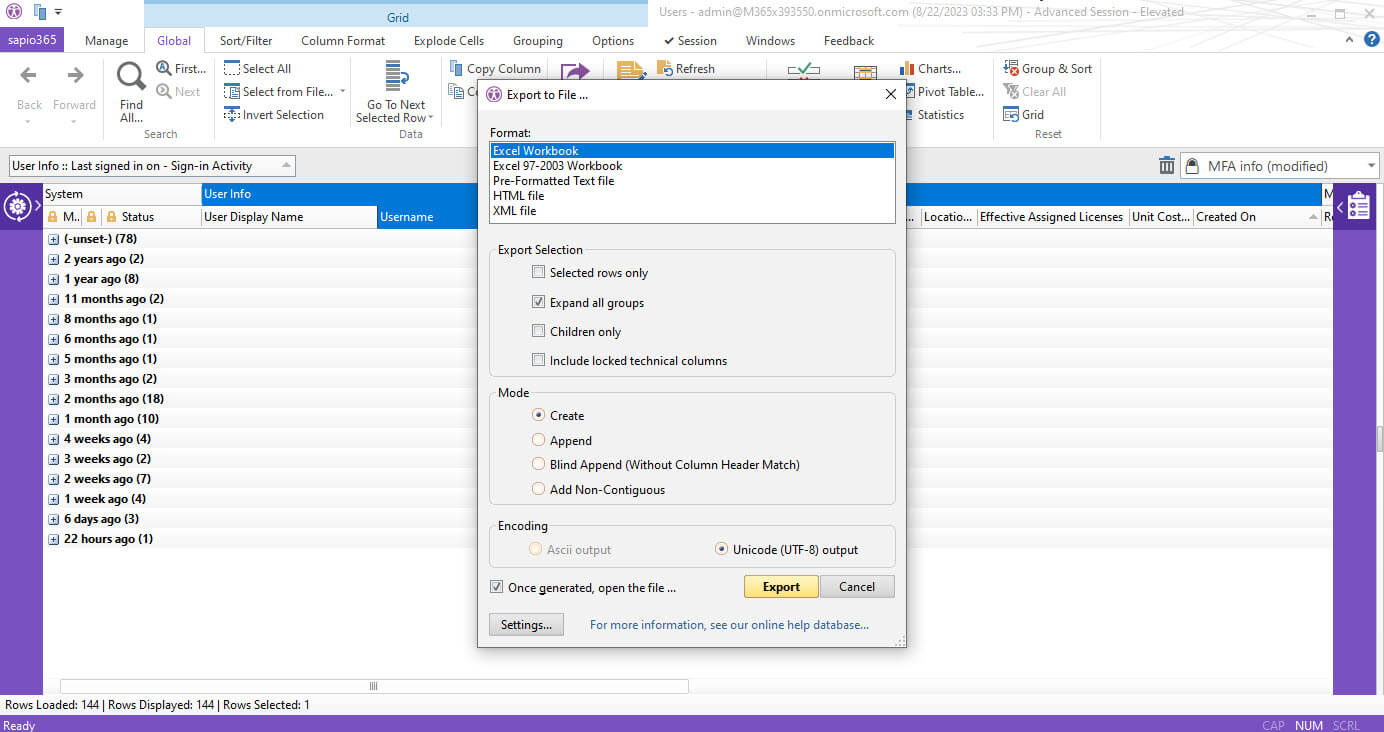
Daphne now wanted to verify the creation dates and login activity for the remaining accounts. There were still some questionable accounts, including those that had never signed in. She exported these questionable accounts to an Excel file and sent it to human resources for verification before she disabled them from signing in.
Regular reporting for ongoing compliance
Daphne loved running scheduled reports and knowing how easy it was with sapio365, she arranged to run a scheduled weekly report that would alert her if any MFA issues reoccurred. MFA issues could include accounts that had not signed-in in over a month, or accounts without MFA registration of authentication methods, making them vulnerable to attack. Running a scheduled weekly report was Daphne’s way of ensuring heightened security on an ongoing basis.
Daphne’s boss loved how quickly and thoroughly he handled this security problem. She managed to lower the risk associated with one of the most common security gaps in Microsoft 365. Daphne told us she is always finding new ways to use sapio365 to solve her IT challenges. Get more detail about Daphne’s process to ensure the correct Microsoft Office 365 multi factor authentication methods were implemented here.
If you have a challenge that you thought was impossible to solve, why not request a demo? Or get a free trial of sapio365 and see what it can do for you!
blog_sapio365

Submit a comment