Removing Weak Microsoft 365 Multi-Factor Authentication (MFA) Methods
Many of our clients struggle to identify at-risk Microsoft 365 accounts and remove weak Multi-Factor Authentication (MFA) methods, especially at scale. While the Entra admin center and PowerShell scripts are viable options, sapio365 offers a more straightforward, no-code way to quickly and efficiently manage all users’ registered MFA methods
Let’s see how they compare!
Or if curious about how sapio365 really speeds things up, skip to the last section or watch the video to see it in action.
Option 1: Managing Registered MFA Methods with Microsoft Native Tools
Administrators can manage and remove users’ MFA methods in Microsoft 365 using either the Entra admin center interface or PowerShell scripts, as outlined in the following sections.
Microsoft Entra admin center
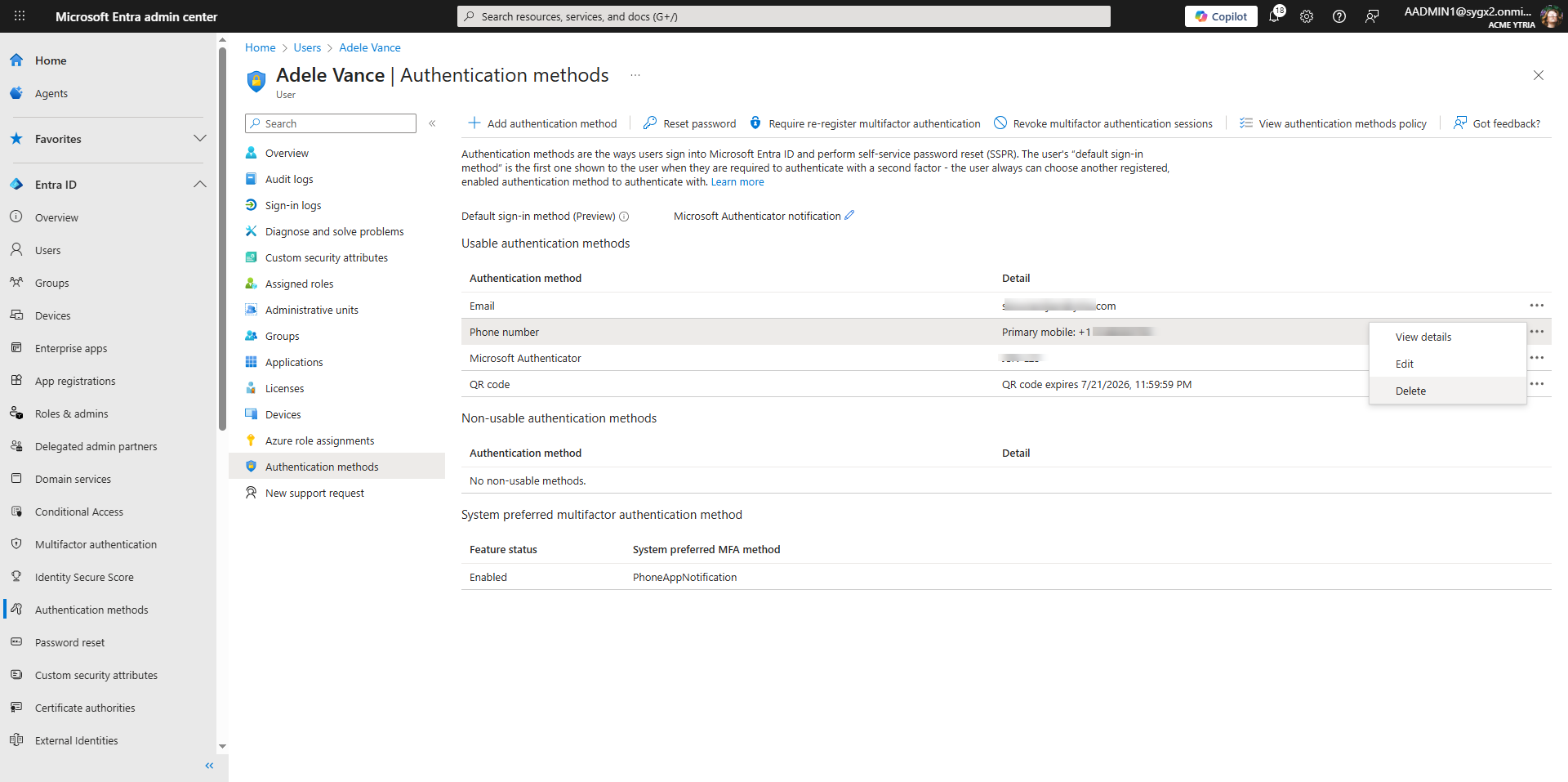
In the Microsoft Entra admin center, you can look up each user’s registered authentication methods.
- Click on a user
- Go to the Authentication Methods blade.
- You can then select each method you want to remove.
The caveat is that you’ll need to repeat this process for each user, as there’s no way to view the global picture of who has what set.
Microsoft Graph PowerShell
Note that admins previously used MSOnline PowerShell to manage MFA before Microsoft retired the module in April 2025.
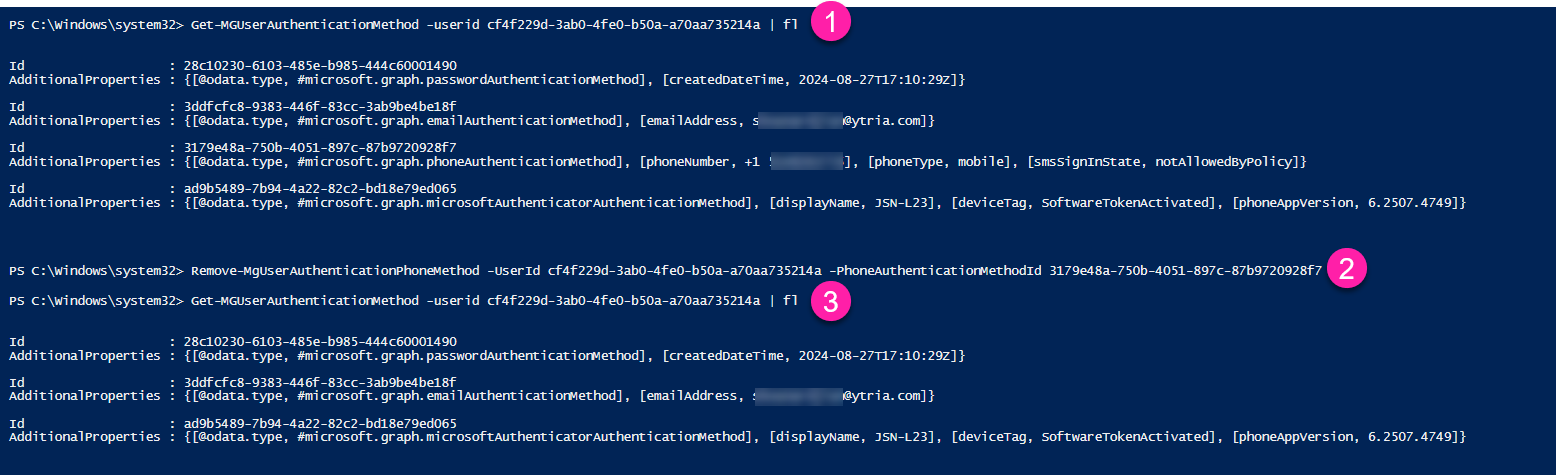
To list a single user’s MFA authentication methods, connect to Microsoft Graph PowerShell. You’ll need one of the permissions as described on this page.
- Then run the following cmdlet to get a single user’s methods: Get-MGUserAuthenticationMethod -userid username@domain.com | fl
- Use the ID of the method you want to remove with this cmdlet: Remove-MgUserAuthenticationPhoneMethod -UserId username@domain.com -PhoneAuthenticationMethodId {some-method-ID}
- Check by running the cmdlet in step 1 to make sure the method is no longer there.
If you want to force a user to reregister, you must remove all his existing authentication methods.
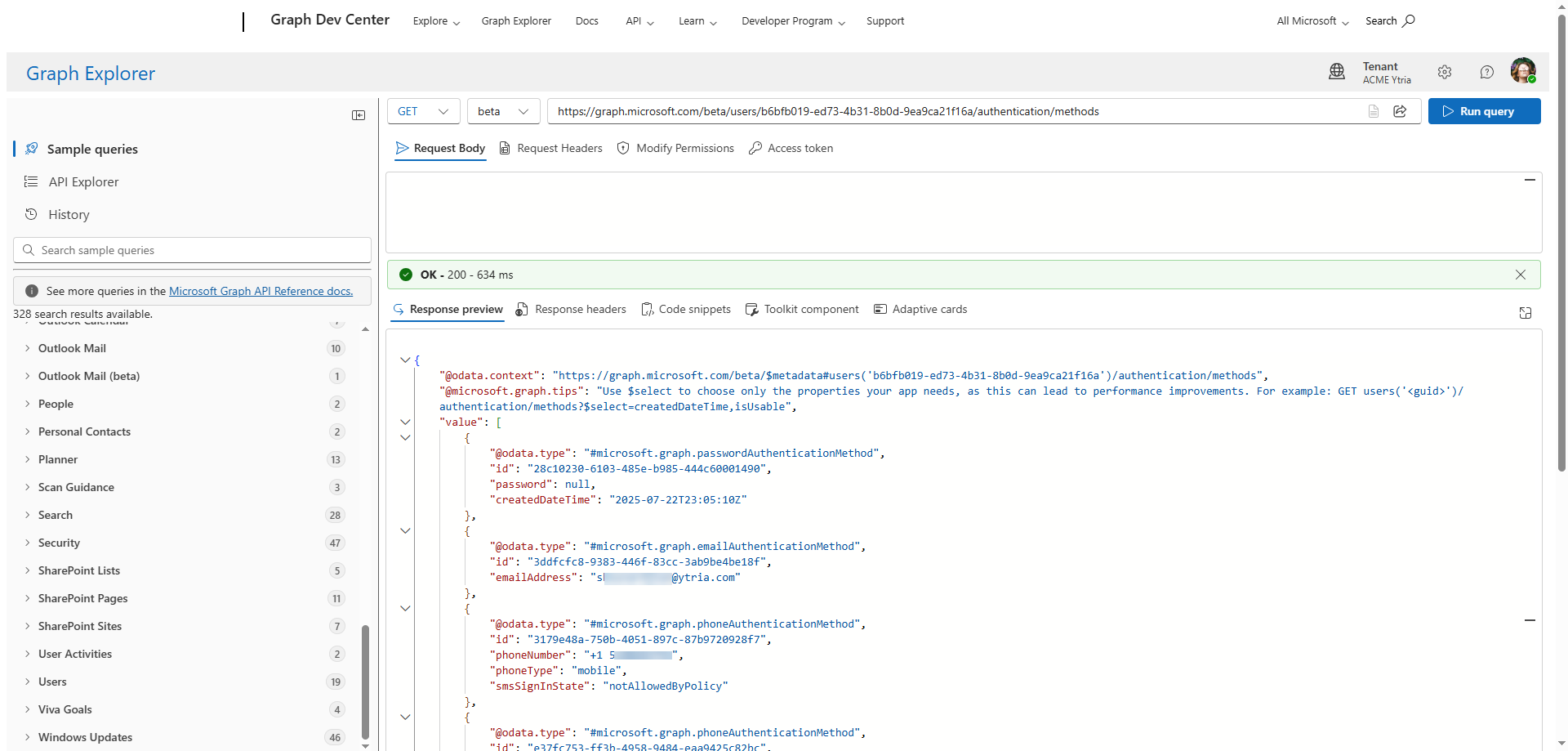
Alternatively, you can also use Graph Explorer to list a user’s authentication methods with the following APIs currently in beta. Note that you’ll need the UserAuthenticationMethod.ReadWrite permission view and make changes – learn more on this page.
See method details with: GET /beta/users/{userID}/authentication/methods as shown in the image below
Just like with PowerShell, to remove an authentication method from a user, you must send a request for each method type using the corresponding method ID.
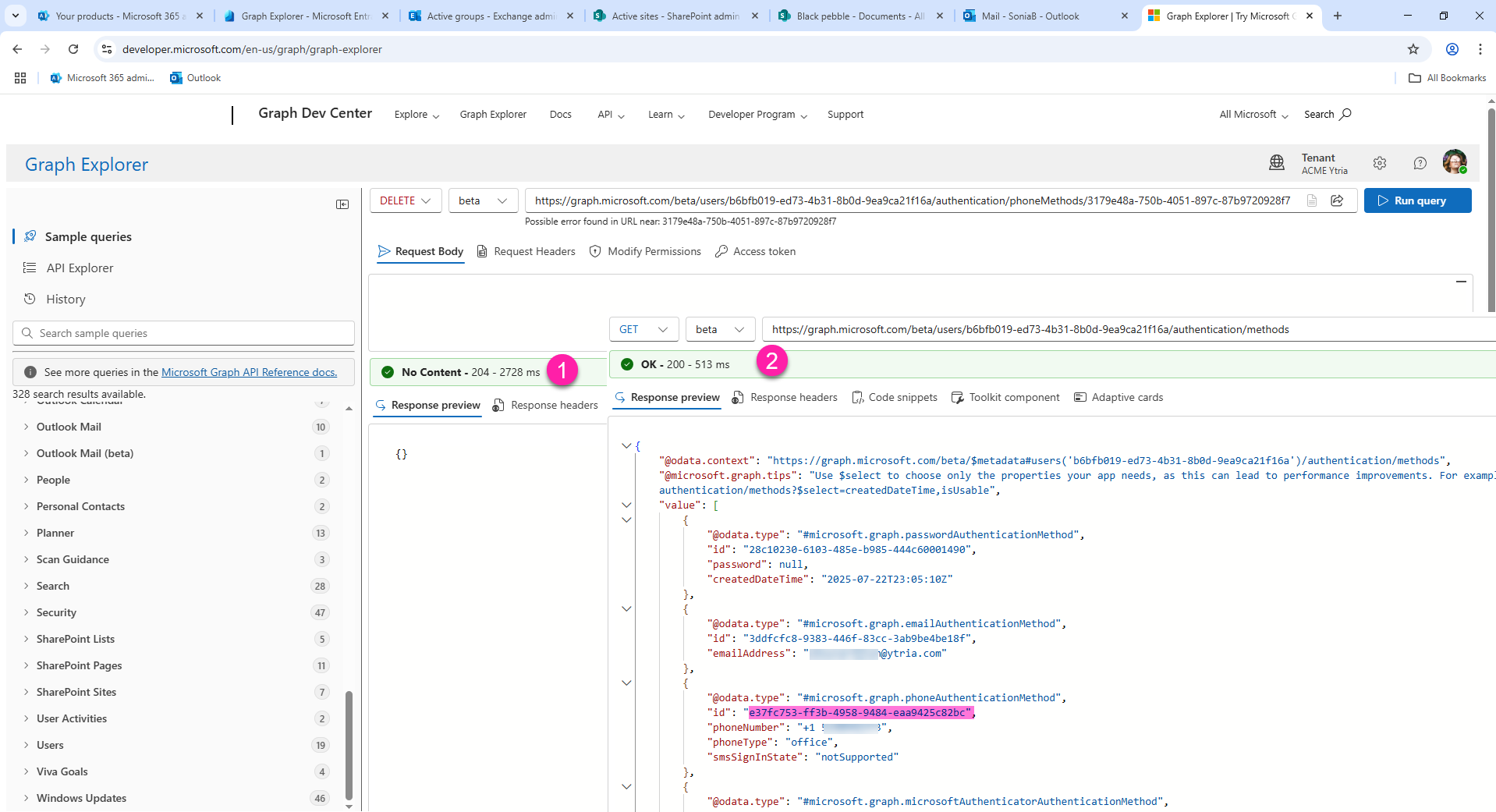
For example, if you want to remove a phone method (including SMS sign-in capability), you’ll need to specify the ID of that method. A user may have more than one MFA phone method registered.
DELETE /v1.0/users/{userID}/authentication/phoneMethods/{phoneMethodId}
The image below shows that (1) a phone method was removed. However, a second phone method (office) with a different ID remains after re-checking (2).
Creating a global report using either of these methods can be challenging, especially when you have hundreds of users. It becomes even more complicated if you want to remove a specific type of method. You’ll need coding skills and quite a bit of patience.
Luckily, there’s another easier option available below!
Option 2: Viewing and managing all users’ MFA methods with a few clicks in sapio365
With sapio365, you quickly get a global, customizable view of all users and their registered MFA methods in one place. You can easily organize and filter the information to fit your needs. When making bulk changes, sapio365 provides a preview of your updates, making the process easier and safer than using PowerShell scripts.
See users’ registered MFA methods in real-time
Once you’ve retrieved your users’ MFA data with just one click in sapio365, you can:
- Apply a built-in view called MFA Method Details to get your report right away.
- Or you can schedule it to send it to any inbox each week.
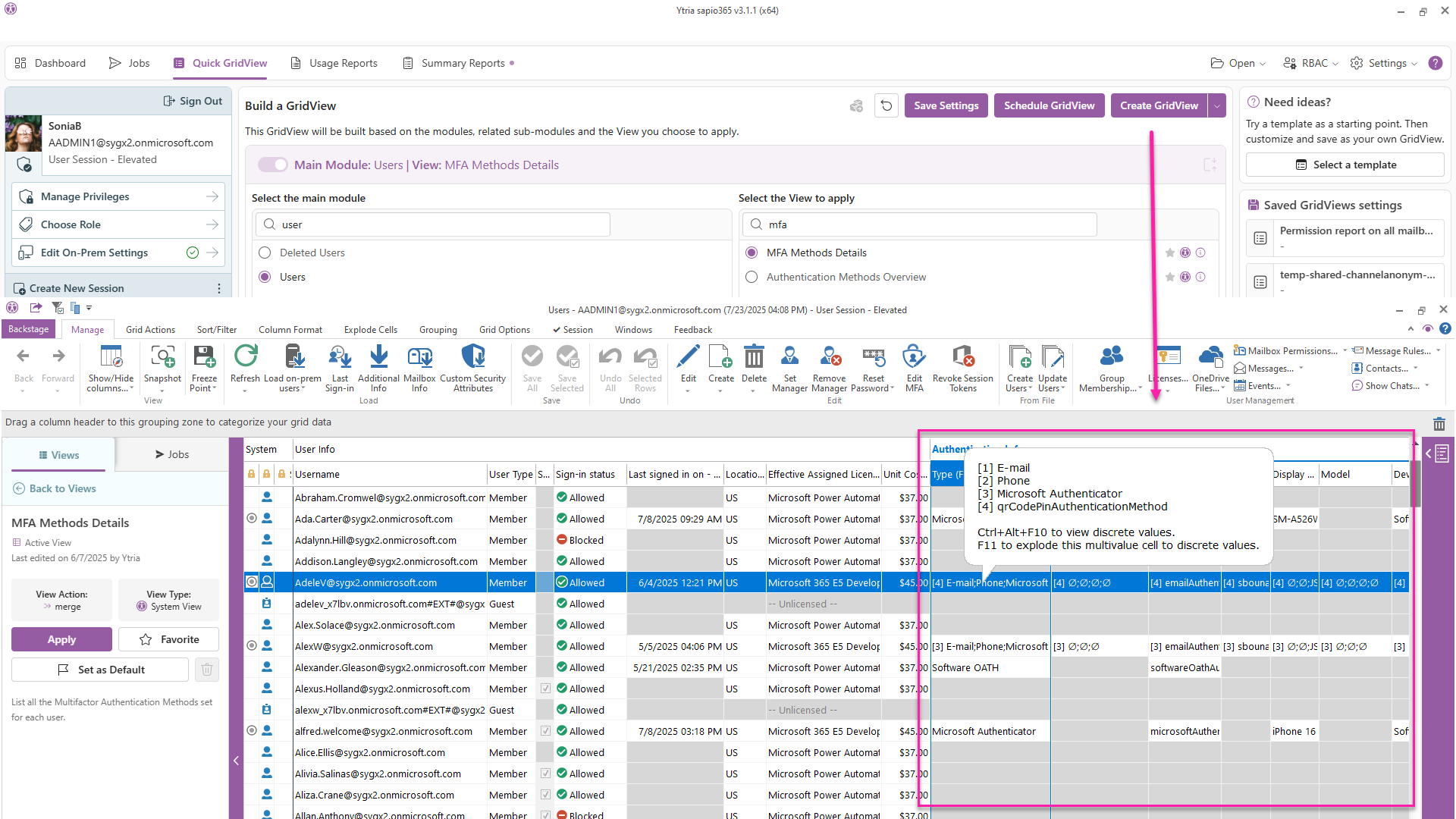
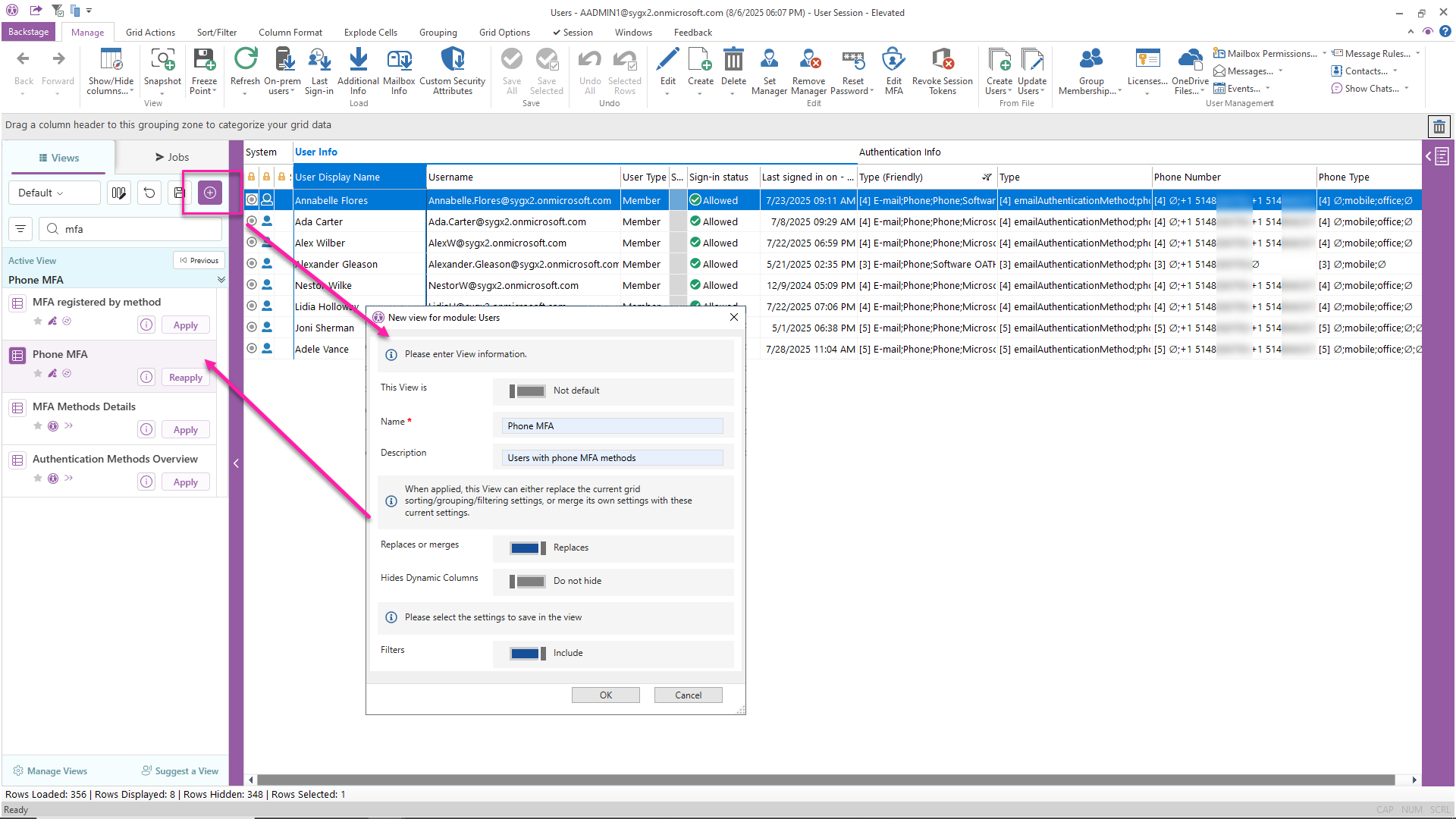
Create a custom, comprehensive view of users’ MFA methods
If you want something more custom, you can use filters, sorting and categorization to isolate users with weak methods (for example, phone methods) – and then save that view!
For example, the image below shows saving a new view of users filtered for registered phone authentication methods and categorized by type.
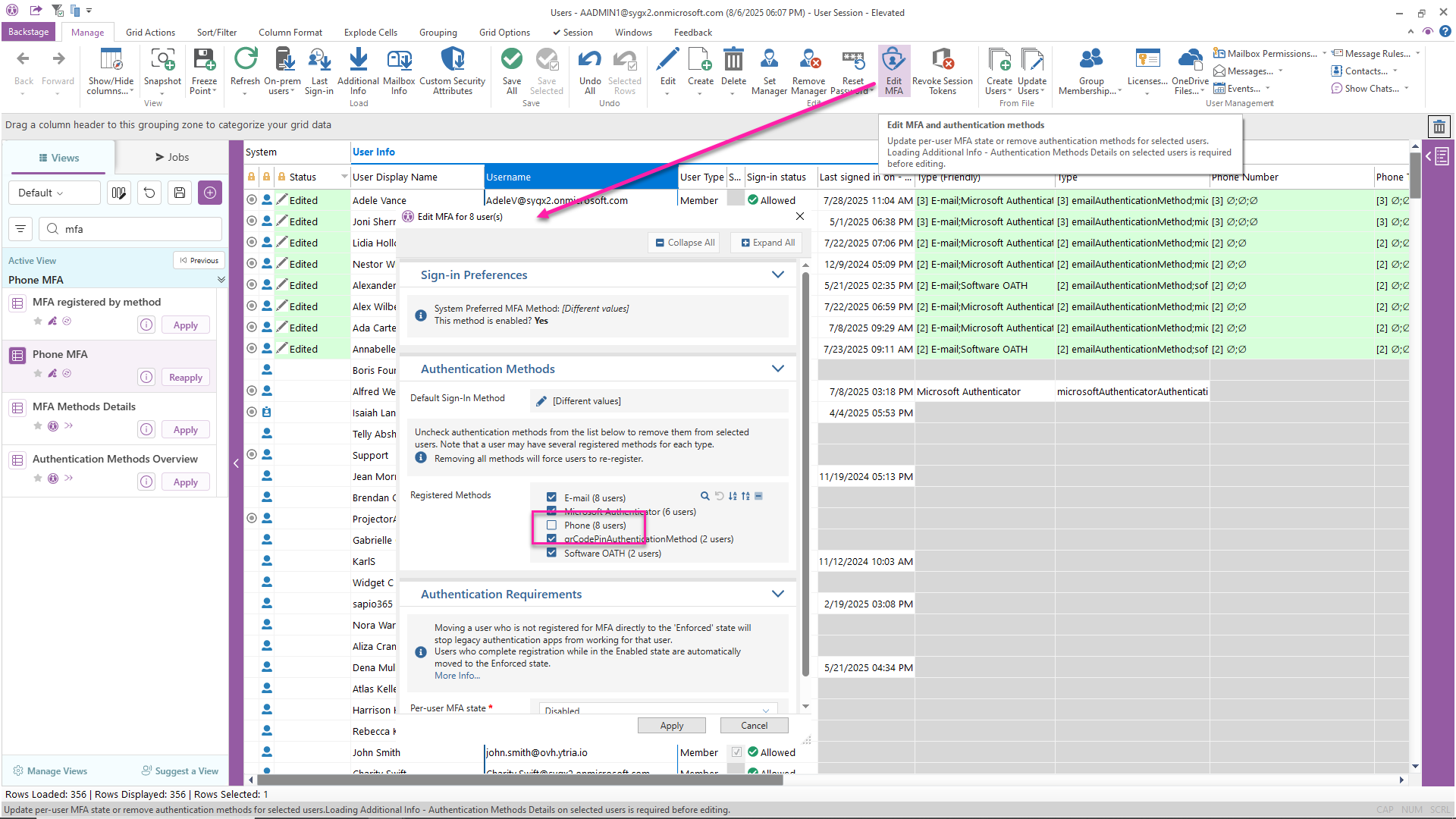
Preview changes when removing weak MFA methods
Once you’ve selected the target users, you can edit their MFA all at once. From the edition dialog, simply uncheck the method you wish to remove from the users. Unchecking all methods will require users to reregister the next time they sign in to Microsoft 365.
If you have 100 users, the whole process will take you less than five minutes.
What’s more, you won’t have to worry about making any manual errors because you can preview all your changes before saving them (remove the filter on the methods!).
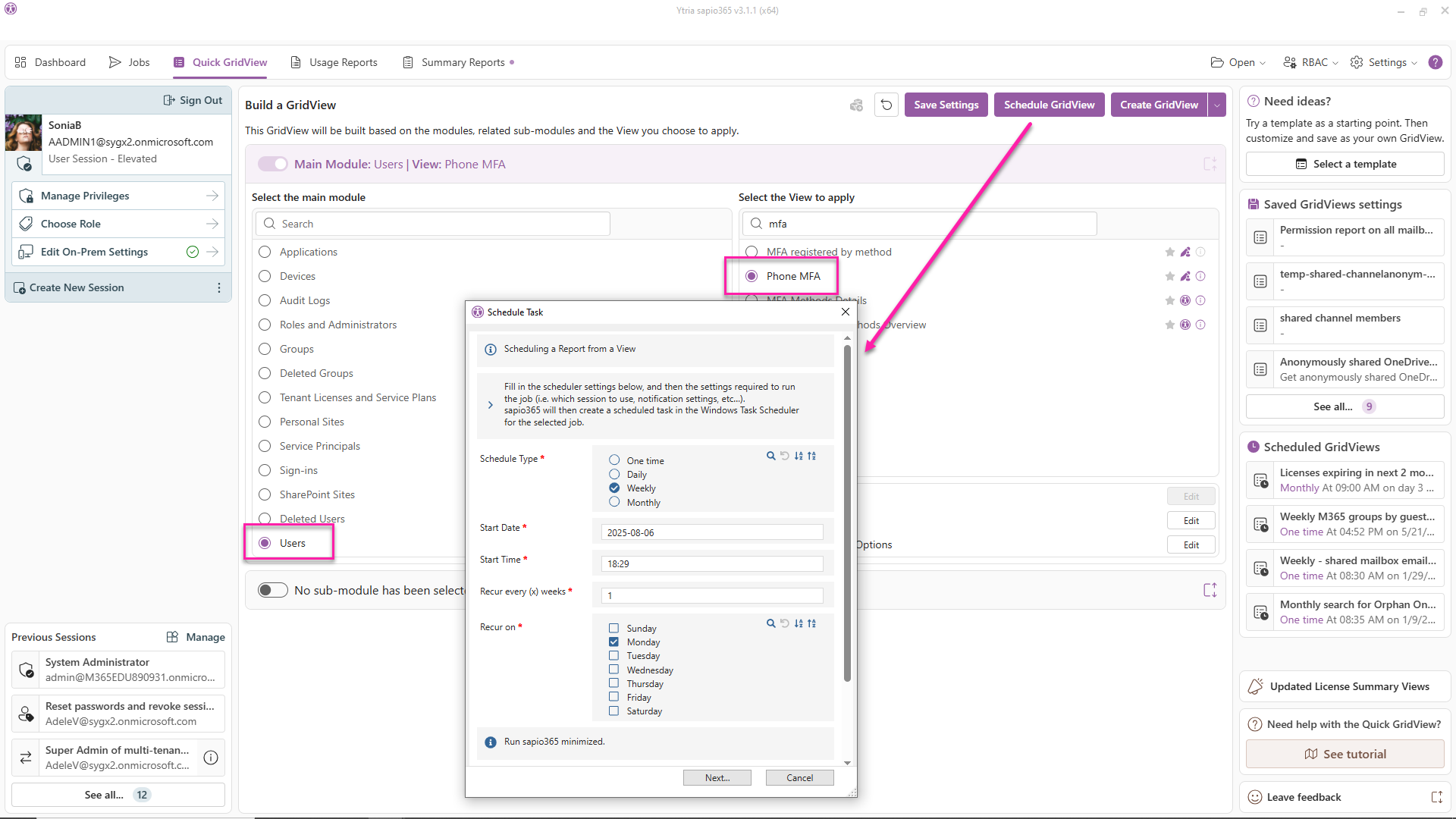
Schedule a weekly report of users with weak MFA methods
Once you have saved a custom view, you’re one click away from setting up a recurrent report delivered to your mailbox every Monday morning.
In summary, with sapio365, administrators can quickly detect and remove weak MFA methods—even without PowerShell skills—improving Microsoft 365 security with minimal effort.
Try it out and let me know what you think.
blog_sapio365

Submit a comment