How you can get picky with regex to isolate all Agent Manager events across multiple server logs
Our support team recently received a pretty interesting request. The user was working in consoleEZ and trying to bring up all events that the agent manager had produced across multiple server logs. A catch was that they didn’t want to include events that contained the “will run on behalf of” AND “ran successfully” strings. To do this, they would have to dabble in regular expressions (regex).
Amgr
Before going any further, a word about case sensitivity: while regex is case sensitive by default, we’ve made regex searches case insensitive for your convenience across the whole portfolio of Ytria tools. However, you can turn the sensitivity back on by selecting ‘Case sensitive’ (see fig. 1).
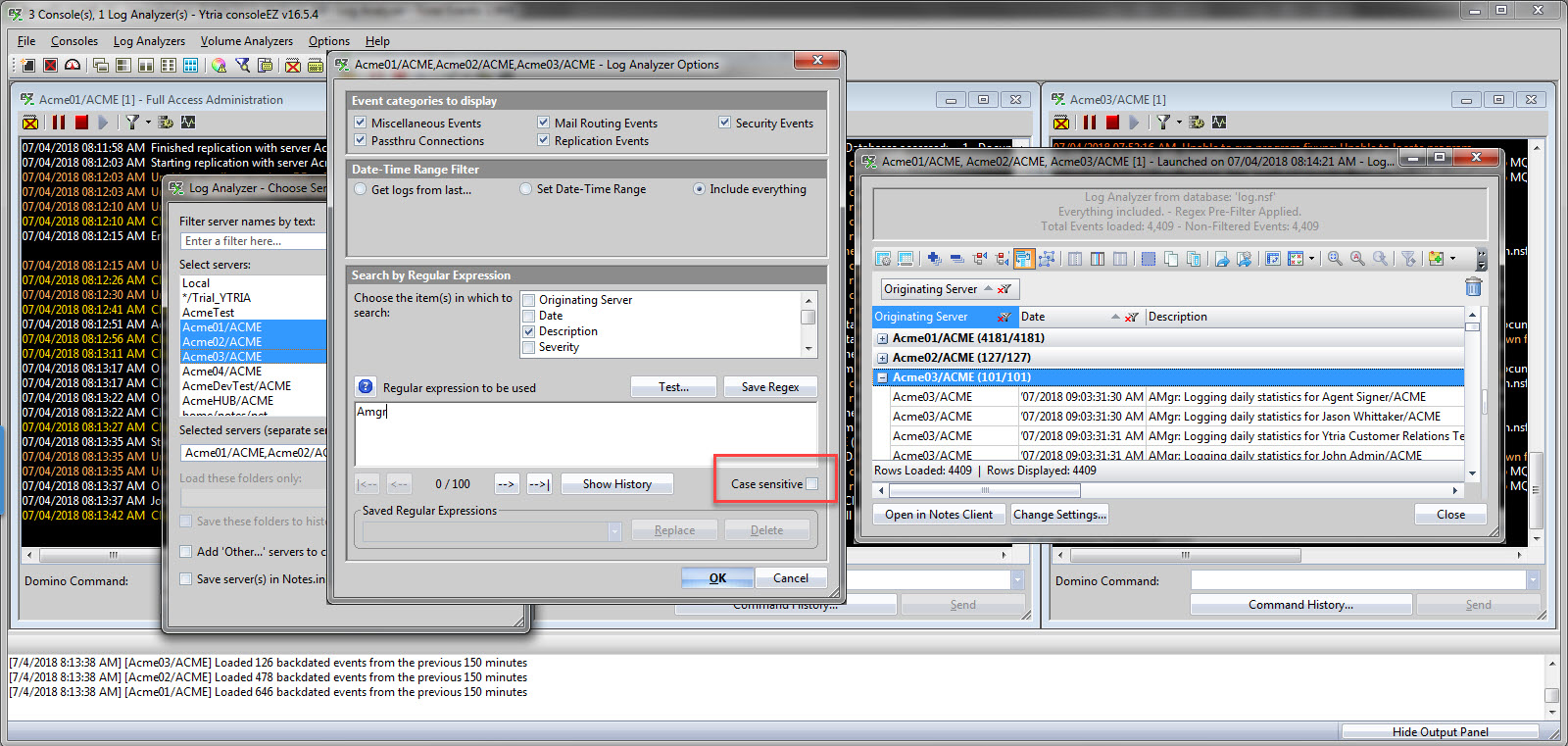
Fig. 1 Regex has been made case insensitive across the Ytria tools, for your convenience. But should you want to turn case sensitivity back on, just select the ‘Case sensitive’ box.
Example 2: filter your consoles’ output to only show events containing the “Amgr” OR “Replicat” strings
Ever wanted to turn your consoles into powerful, real-time agent manager and replication event monitoring tools? No problem! Simply open consoles to all servers that you’re interested in, and then select ‘Consoles > Filter Consoles By’ and provide the following regex (see fig. 2):
Amgr|Replicat
You can also use this very same expression for log file searches.
Note: when using regex to filter your consoles, you have the additional option to ‘Show’ or ‘Hide’ the results returned. So, in this example choosing ‘Show’ will leave only the events containing the “Amgr” or “Replicat” strings. If you were to choose ‘Hide,’ that same regex would hide all these events.
Example 3: search your server logs for all events that contain both the “Amgr” AND “cannot” strings.
Let’s say you want to locate any agents that aren’t properly signed, and therefore aren’t allowed to execute on a given server. This is a bit more complex. Because to find these, you’re going to need a search regex that will find any events containing the “Amgr” string AND part of the typical error message, for example, the “cannot” string.
Essentially, our expression needs to say “contains string A” AND “contains string B”. For adding conditions that must be true altogether, you’d use the following syntax:
(Condition1)(Condition2).*
Quite similar to selection formulas, right? Independent conditions within parentheses.
How would that look in real terms?
(?=.*Amgr)(?=.*cannot).*
Add that into your Log Analyzer regex input (see fig. 3). We’ll look a bit more at what those special characters mean in the next example.
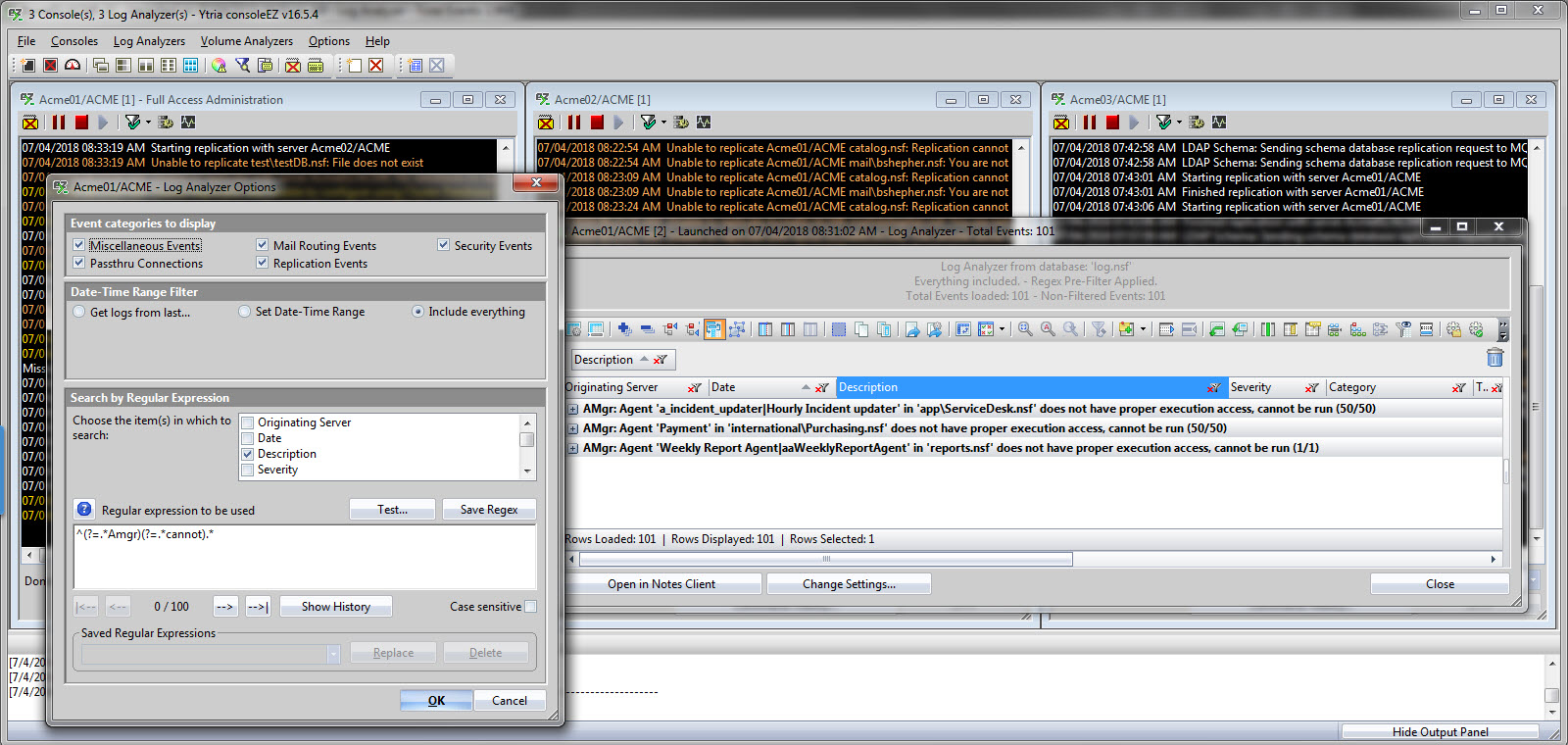
Fig. 3 To find both the strings “Amgr” and “cannot”, enter the following into your Log Analyzer regex input ^(?=.*Amgr)(?=.*cannot).*
Example 4: search your server logs for all events that contain “Amgr” but DO NOT contain the “run on behalf” string.
When you search for all events containing the “Amgr” string, you’ll notice that a lot of non-critical info is returned. If you’re interested in those more problematic messages, you might want to cut down on the noise.
Let’s see how you can use regex to search for string “A” while excluding results that contain string “B”:
^(?=.*Amgr)(?!.*run on behalf).*
So, what’s going on here?
Example 3 and the first part of this example both contain the expression ?=.* to find what contains the string “Amgr“. And this example adds in the expression ?!.* to find what does not contain the string “run on behalf“. So, our results here will be events that contain the string “Amgr” AND that don’t contain the string “run on behalf“.
You’ll see that even with this search, you’ll still get a ton of useless messages. To further cut that down, you can add even more exclusions such as the “daily statistics” or “Start executing” strings. And since you can just keep appending more conditions by enclosing them in parentheses, let’s see how that looks (see fig. 4):
^(?=.*Amgr)(?!.*run on behalf) (?!.*daily statistics) (?!.*Start executing).*
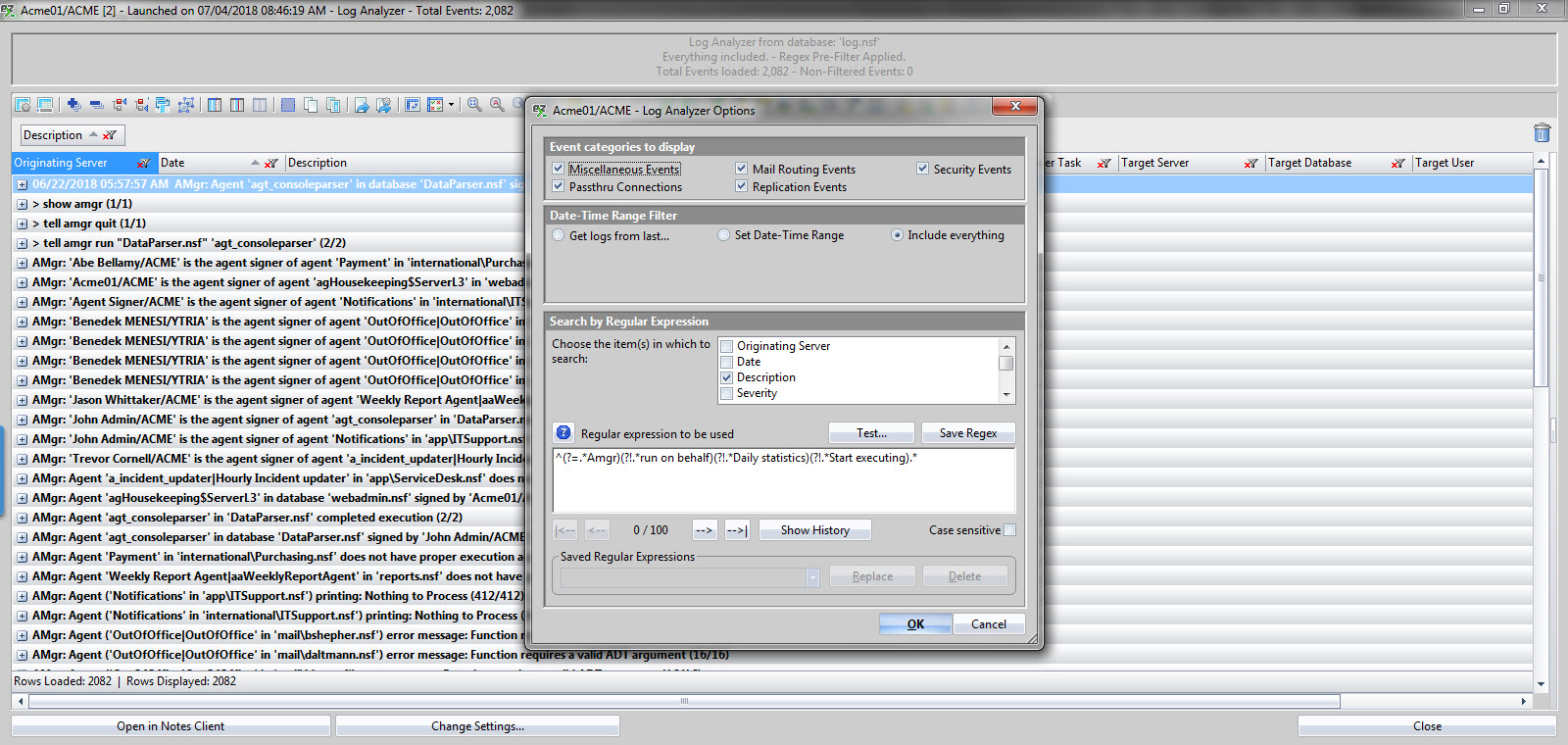
Fig. 4 Append more conditions by enclosing them in parentheses.
We hope you found this helpful. You have some quick and useful examples to help you get going with regex searches in consoleEZ’s Log Analyzer, and also a bit of a basic regex background for a couple of expressions you can use elsewhere, should you need to.
Do you have any scenarios we can help with? Shoot us a quick mail, or put your request in the comments section. We’d be happy to give you a hand with it!
Intrigued, but don’t have consoleEZ yet? Give consoleEZ a try.

Submit a comment